Why Proof of Stake?
Similarly to Proof of Work, Proof of Stake is a blockchain network consensus algorithm. First introduced in 2011 on Bitcointalk forums, it was designed as an alternative to PoW and a remedy to its underlying issues.
The main idea behind PoW is to have blockchain nodes perform computationally expensive operations to verify transactions and mine new blocks. As the nodes compete with one another, the energy cost of these operations grows rapidly, and if a solution is found too quickly, the system will raise the difficulty of subsequent verification operations. This makes the algorithm’s power consumption extremely high, which in turn led to the emergence of an entire industry dedicated to manufacturing equipment optimized for Blockchain mining.
The makers of Proof of Stake concluded that the existing mechanism was not good enough, and an alternative solution was necessary.
How does Proof of Stake work?
In the Proof of Stake algorithm, the validator of the new block is selected randomly from among the nodes that hold and deposit as a stake the minimum number of tokens required in the given network. The number of tokens staked raises a participant’s chances of being chosen. Accordingly, richer players stand a better chance of being selected as the validator of subsequent blocks and transactions. Additional criteria are used to prevent the wealthiest nodes from monopolizing the consensus mechanism and the associated transaction processing fees. The most popular of them include:
- randomized block selection
In the above mechanism, the selection of the next forger (in PoS blocks are minted or forged, not mined like in PoW) is based on the combination of the lowest hash value and the highest number of staked tokens.
- coin age-based selection
Coin age considers the time tokens have been held as stake for network verification purposes. This prevents situations where large numbers of tokens are staked for a brief moment to boost the short-term chances of earning fees. In most cases, they must remain locked for at least 30 days before they can be staked again, as represented by the formula below:
Chance of selection = number of tokens x coin age (days since tokens have been put up as stake)A quick look at the formula above shows that fewer tokens staked for a longer period can be equally effective as their greater number staked for a shorter period.
After being selected, the coin age is reset and a specific minimum wait time is required before the node can participate in forging again.
It is easy to notice that the assumptions of the coin age algorithm prevent a monopoly of the richest nodes because even if they are selected, they cannot be re-staked before a certain amount of time has passed.
In Proof of Stake, the selected block validator is rewarded with a commission fee, which serves as an incentive and attracts participants willing to meet the assumptions of the decentralized network.
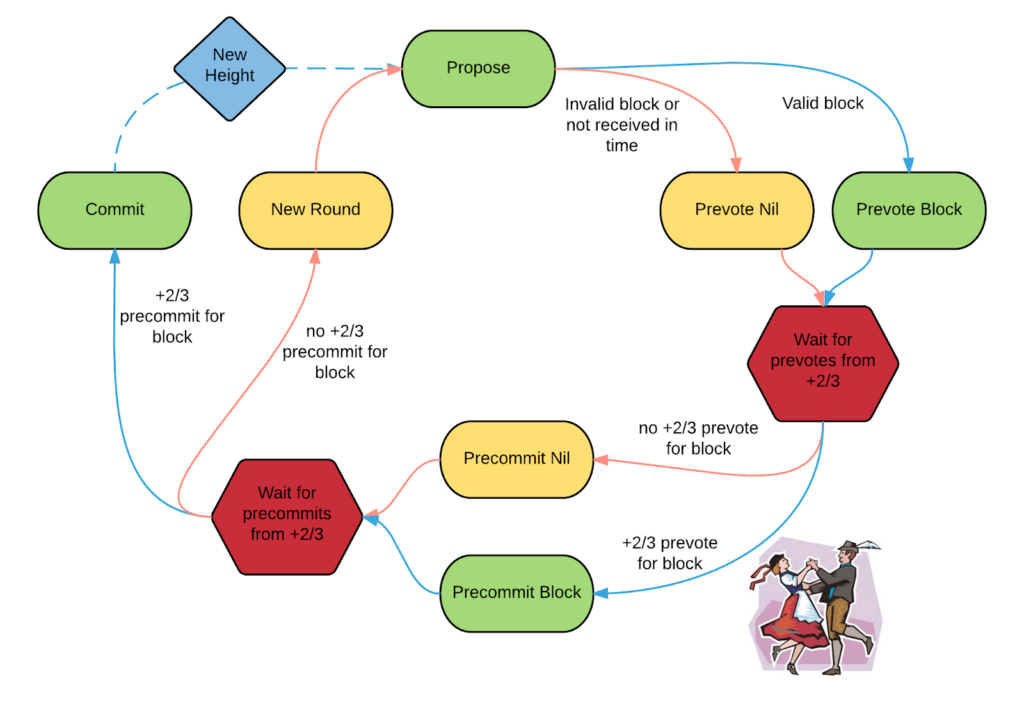
Tendermint, based on, among others, the Cosmos network, serves as a good illustration of the PoS algorithm.It is a popular variant of PoS based on BFT (Byzantine Fault Tolerance), relying on an easy-to-understand state machine and voting mechanism.
Tendermint is a turn-based mechanism of voting on changes in the Blockchain network with each turn comprising 4 phases: propose, pre-vote, pre-commit, and commit.
Participants are called validators, and each round of the algorithm goes as follows:
- A selected network participant (proposer) is selected to propose a new block with defined H (height) and R (round) parameters. The proposer is selected in sequence based on its stake in the network (number of tokens held).
- If the proposer did not exceed the time allotted for this phase (was not timed out) and the block has the correct parameters, the pre-vote phase is started.
- The remaining nodes (validators) must decide whether to accept the proposed block. If the validator is not locked on a block since the previous round of the algorithm and concludes that the properties of the newly proposed block are correct, it broadcasts acceptance of the block to the network in the pre-vote phase. Otherwise, the validator rejects the proposal by broadcasting the nil value. Next, the network transitions to the pre-commit phase.
- Blocks broadcast their decisions taken in the pre-vote phase all over the network so that each participant is made aware of its peers’ decisions.
- If a given validator concludes before the timeout that more than ⅔ nodes in the network (at least ⅔ + 1) accepted the proposed block, it broadcasts approval for the pre-commit phase. In this step, each node verifies the votes of the remaining network nodes. If this phase fails, the validator rejects the block by broadcasting the nil message for the pre-commit phase.
- If the network receives ⅔ + 1 message accepting the pre-commit phase, it accepts the block and appends it to the blockchain. Thus, the network enters the commit phase. Otherwise, the proposer proposes a new value, and the entire process is restarted.
It is readily noticeable from this description that Tendermint operates correctly as long as the number of malicious or defective network participants stays below ⅓ and is thus considered a BFT algorithm.
Staking
Staking is the main consensus and transaction verification mechanism in Proof of Stake based networks and involves locking funds in a special wallet. Staking our cryptocurrency adds us to the pool of network participants who stand a chance of being selected as the validator of the next block and thus earn a certain number of coins as transaction commission.
Amid an environment of low-interest rates and scarcity of alternatives offering a similar return on investment, staking is quickly gaining popularity. Staken funds can be withdrawn but become accessible only after some time has passed.
This wait time depends on the specific implementation of the consensus algorithm in a given blockchain. Staking is done using so-called smart contracts, with their operation varying between different networks, e.g. unlocking an EOS token takes 72 hours, but a DOT token requires 28 days to become accessible.
Examples of existing staking mechanisms:
Ethereum 2.0
Coin staking in Ethereum 2.0, the most popular PoS-based chain, requires a minimum deposit of 32 ETH (some USD 56,900 as at 22 March 2021), making the barrier to entry very high.
The expected annual return on staking is around ~ 8% (source: stakingrewards.com)
Tezos
The minimum number of XTZ coins to start staking is 1, which, given its price as at 22 March 2021, is equivalent to only USD 4.28.
Expected annual return on staking: 6% (Source: ledger.com)
Cosmos
One of the most popular projects based on IBC (Inter-Blockchain Communication) also offers a staking option. The minimum stake is 0.05 ATOM (~ USD 1.04)
Expected annual return on staking: 8-10% (Source: ledger.com)
Polkadot
Another popular IBC-based project. The minimum stake is 350 DOT, i.e. around USD 11,000.
Expected annual return on staking: 13% (Source: ledger.com)
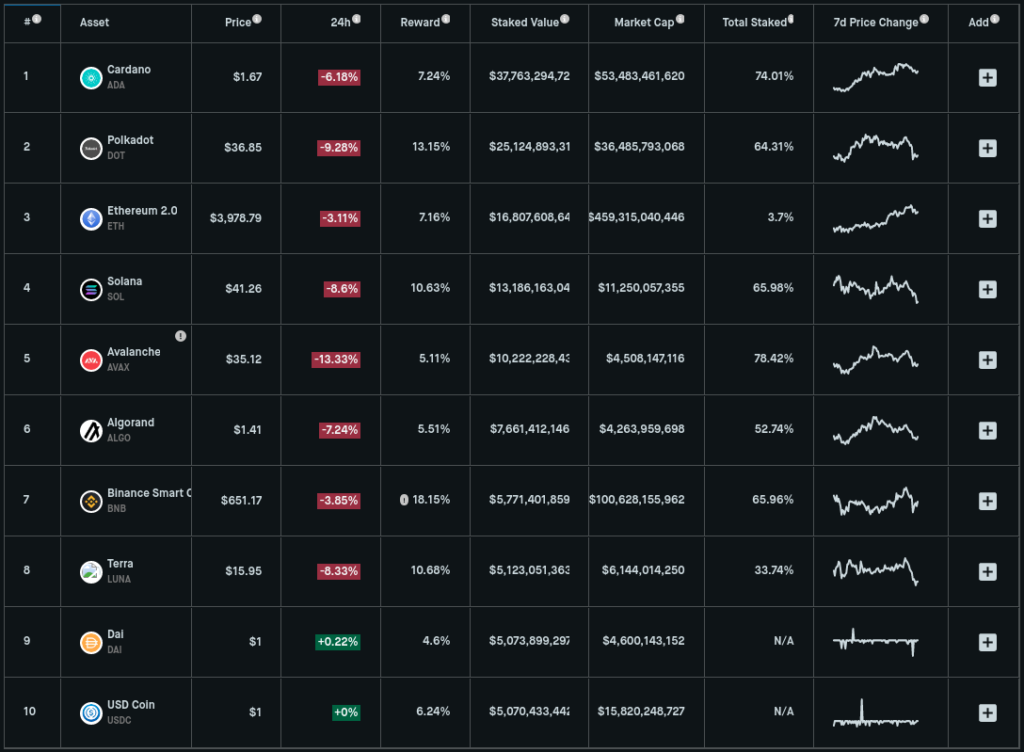
Examples of rewards for staking in the 10 most popular coins are presented in the table:
The mechanism outlined in this paragraph is perfectly illustrated by the following diagram:

Security
Many people ask themselves whether tokens are safe in PoS-based networks? In truth, PoS, as a mechanism, is a bit younger than the PoW, which makes it less battle-tested by attackers.
Slashing
Slashing is an anti-fraud mechanism. Suppose the network detects that a given node validated a fraudulent transaction. In that case, some of the funds staked by the node will be lost (a mechanism called slashing). The participant caught engaging in fraudulent activity will be excluded from participation in the forging of future blocks.
51% attack
For one malicious participant (or an organized group) to take control of the network, it would have to hold most of the existing tokens in a given blockchain – this type of attack is called a 51% attack or a majority attack. An attacker able to gain such control may, for example, influence the consensus algorithm, engage in double-spending, and monopolize the forging of future blocks.
Though profitable in theory, the cost of carrying out such an attack on an established blockchain would be huge, rising in proportion to the size and popularity of the network.
To carry out a 51% attack, the attacker would have to aggressively buy tokens on various crypto exchanges, inflating their price and exposing him to considerable cost. Even if successful, the network could be simply rolled back to its state before the attack, forcing the attacker to re-incur all the associated costs should he try to repeat the attack.
Proof of Work vs Proof of Stake
Many blockchain creators are still asking themselves which mechanism is better. The answer, as usual in such situations, is: it depends 🙂
Energy
The PoW mechanism requires vast amounts of energy to operate on a large scale. As shown here, the entire Bitcoin blockchain currently has a higher energy consumption than Sweden and Ukraine!
This is because PoW requires participants to perform expensive cryptographic computations to mine a new block. These calculations become more difficult as the network grows. The analysts estimating that when the price of Bitcoin breaks the USD 1 million mark, the entire network will use more energy than the US!
PoS does not require anywhere near that much processing power. Participants do not have to compete on speed of operations using purpose-built and power-hungry hardware. Rather they are selected randomly by the blockchain. Hence, the creation of blocks is referred to as forging, not mining.
If the node selected in the draw behaves dishonestly, e.g. validates a fraudulent transaction, it is punished through slashing.
Security
PoS is also more resilient to the 51% attack. Suppose an attacker on a PoW-based network bought a massive amount of mining rigs (computers built for the sole purpose of mining) and decided to launch a 51% attack on a network. If he succeeds, rolling the network back to its state prior to the attack will not stop the aggressor from attacking again. After all, he already has the equipment and skills, there’s nothing stopping him.
To launch an attack on a PoS-based network, the attacker must first buy the majority of tokens existing in the network, and, in the case of a rollback, he will be forced to re-incur this expense.
Proof of Stake is most vulnerable to so-called nothing at stake attacks. Such attacks are possible by forking the network, i.e. copying the given blockchain with its entire history and forging blocks on several copies simultaneously.
PoW is much more resilient to this type of attack as the attacker’s processing power. It would have to be split between the number of network instances he intends to attack, significantly impairing his ability to mine new blocks.
This safety measure does not work for Proof of Stake. If we buy tokens and participate in validating a network, every subsequent copy will have the same history. This enables the attacker to perform multiple operations based on only one-time staking in the original Blockchain version.



